Data Management
/Research Curation Team:
Cecil Chua (Missouri University of Science and Technology, USA), cchua@mst.edu
Marta Indulska (The University of Queensland, Australia), m.indulska@business.uq.edu.au
Roman Lukyanenko (HEC Montréal, Canada), roman.lukyanenko@hec.ca
Wolfgang Maass (Saarland University, Germany), wolfgang.maass@iss.uni-saarland.de
Veda C. Storey (Georgia State University, USA), vstorey@gsu.edu
Download the Data Management Curation
Download the Infographic
Download the References (in EndNote and BIB formats)
In our modern, digital world, the critical role of information technology makes data management an important research topic. This paper curates data management research at MIS Quarterly as it has progressed from its early context of understanding requirements of relatively simple information systems to the sophisticated and complex systems of today. In the following sections, we discuss the focus of this curation, the themes of data management, and the progression of research over time. We reviewed each paper published in MISQ since its inception, assessing the paper's relevance to the curation's theme. Because of the ubiquity of the word ‘data’ in MISQ papers, we performed this review manually rather than relying on keyword searches. We iteratively classified the relevant papers into 5 themes based on consensus. Our final curation includes 81 papers. To keep the text concise, we eschew citations from the paragraphs below and instead include them in the associated tables that follow.
1. Focus of Research Curation
Nearly all aspects of business and society are affected by initiatives involving the capture, storage, and use of data: artificial symbols that are employed to represent states of reality. With the increased reliance on digital data (symbols represented via binary code), the field of data management emerged in the 1970s: the same decade in which MIS Quarterly was launched. In fact, the first issue of the journal included a paper on data management. Since then, data management has become increasingly important. With organizations embarking on digital transformation programs, data has become a central driver of how organizations operate and are managed.
2. Themes of Data Management
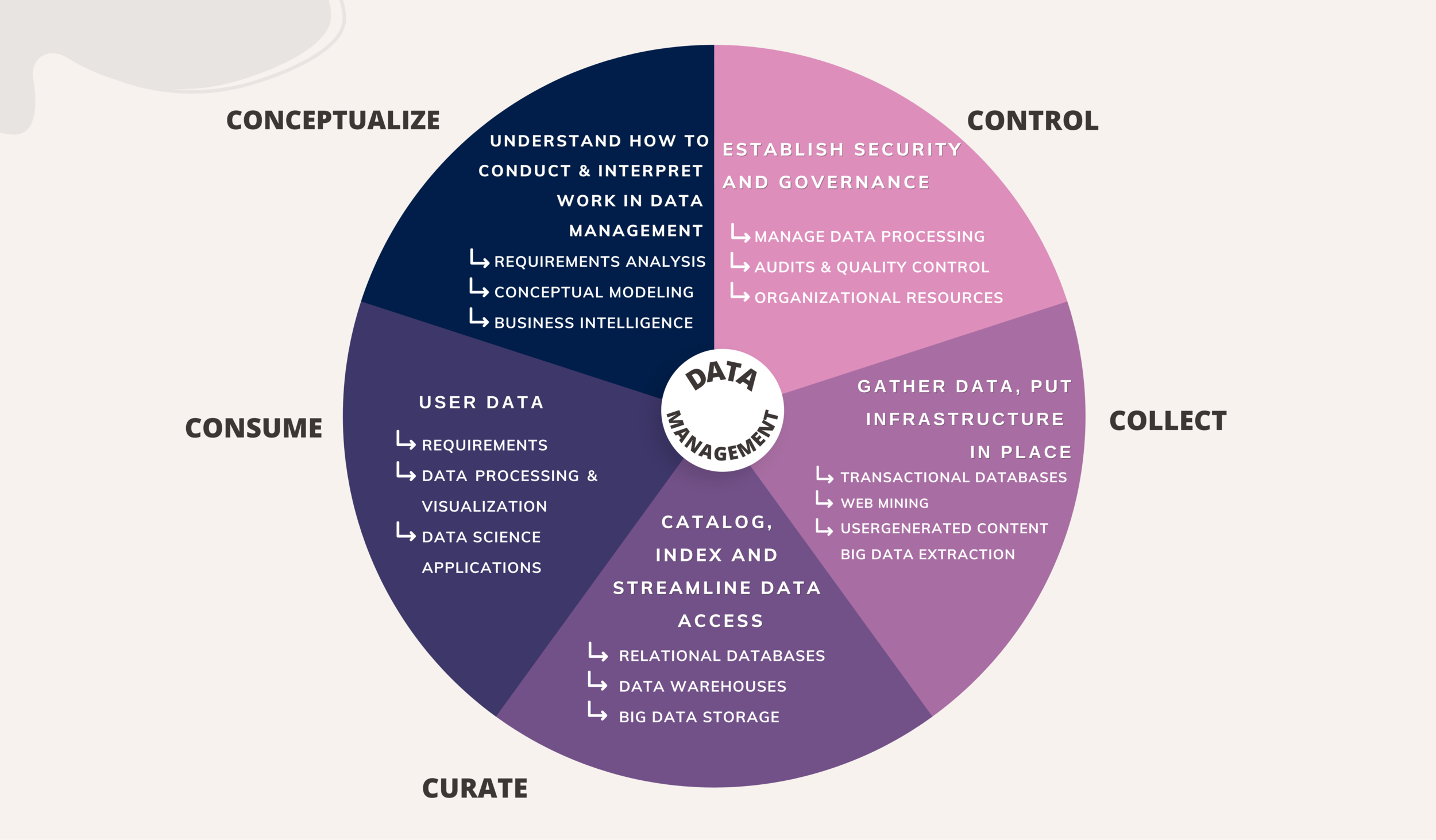
We define the field of data management as an area of study that investigates and develops activities and methods to conceptualize, collect, curate, consume and control data to support insight, analysis, and action. We, thus, establish the 5Cs of Data Management, shown in Figure 1 and use them to classify the significant research that has been carried out in information systems, as reported in MIS Quarterly.
Figure 1. 5Cs of Data Management
2.1 Conceptualize
Conceptualization is an activity that analyzes and represents (e.g., using concepts such as conceptual schemas, relationships) an existing situation, problem, or process. In the information systems field, conceptualization research has focused on eliciting information requirements, defining the data creation process, and supporting the design and implementation of information technologies. The most prominent research has focused on developing methods for requirements elicitation and analysis, and developing and evaluating conceptual modeling approaches. The latter lies at the core of “conceptualize” because it enables the graphical representation of requirements identified through the requirements elicitation process. Conceptual modeling supports information systems development, especially database design and project management, by defining the scope of a system in terms of its data and functionality.
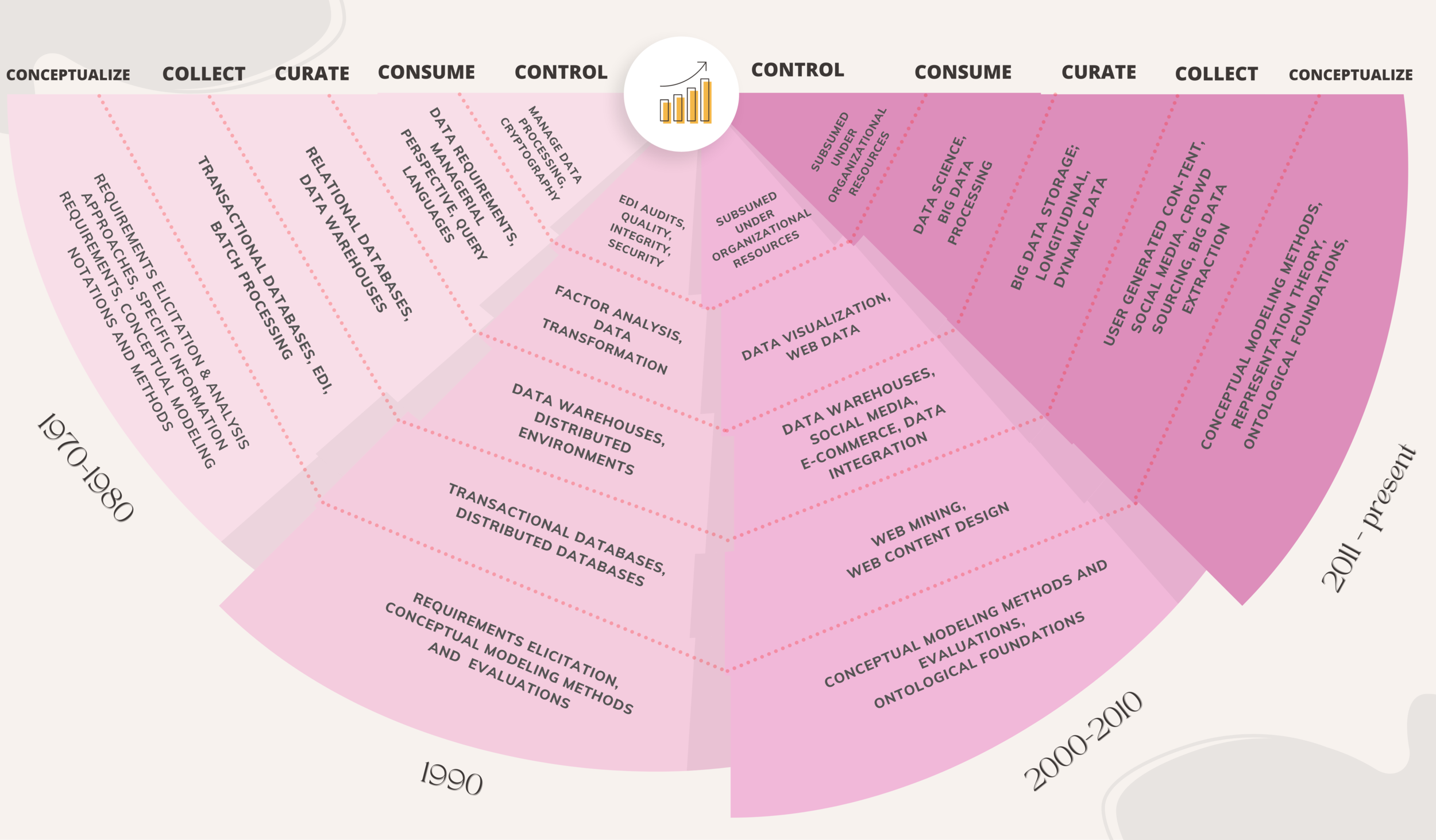
MIS Quarterly contributions to the “conceptualize” aspect of data management research began in the 70s and 80s and focused on ensuring that information systems meet the data requirements of their users, either through improving methods for requirements elicitation or by identifying specific information requirements. During the 1990s, there was a continued focus on identifying information requirements for specific roles as well as comparisons of various requirements elicitation methods and tools. The introdution of the world wide web led to research on hypertext databases. In the following decade, a shift within conceptualize-related research occurred, moving it towards developing and evaluating conceptual modeling notations and methods. In the last decade, MIS Quarterly has continued its consistent focus on conceptual modeling and saw the return of the identification of requirements for specific contexts or types of systems.
2.2 Collect
Collection is a data management activity to identify suitable sources of data, design data collection or data extraction and integration protocols, and establish quality and other controls over data collection and acquisition. Data collection may involve creating new data or acquiring existing data, such as extraction of data from a website. Major challenges and solutions related to data collection emerged in 1970s and 80s. The challenges of data collection focused on the needs of the emerging applications of technology, such as relational databases and electronic data interchange (EDI). Studies focused on supporting transaction processing, batch processing, and recording unanticipated (“special event”) data. Issues of data collection gradually transitioned from a pure technological focus to an organizational imperative, supported by research on the costs related to poor data collection and the consequences of poor data collection practices.
In the 1990s, research continued to investigate data collection in transaction processing systems, but with greater emphasis on distributed processing. The next decade can be characterized by a focus on web technologies, their design and content extraction. With the rise of the world wide web, researchers started to consider challenges associated with ensuring high data quality, and collecting large amounts of data from customers on the Internet. Over the past decade, research continued to focus on the design of collection and extraction mechanisms of existing data on the Internet. With the increasing volume and societal value of user-generated content, research investigated the collection of varied and heterogeneous data from online users. Other studies continued to apply natural language processing techniques, increasingly supported by data intensive machine learning approaches, such as deep learning neural networks.
With the evolution of technologies and new methods to collect data, a parallel evolution of the roles related to data collection occurred. Thus, initially, data collection was a concern for database designers, auditors, and managers overseeing the process. With the diversification of data sources, many others began involved in data collection activities, including programmers and engineers tasked with extracting data from external sources, data scientists attempting to reuse existing data, and ordinary people, who are the providers of user generated content.
2.3 Curate
Curation, as a data management activity, involves the development of both physical and logical infrastructures that make it feasible to collect, index, and store data, and facilitate data access for subsequent analysis. The curation of data involves categorizing and organizing data so it can be easily shared. Specific activities include: designing data storage systems, such as databases; cleaning and transforming data to ensure it can be stored in existing data storage infrastructures (e.g., relational databases); cataloguing and indexing data to facilitate subsequent retrieval; and ensuring appropriate security of data storage systems. Data curation is dependent upon the goals for subsequent use. Various techniques and approaches convert data into a usable form and store it in data warehouses, so it can be used for a wide range of purposes.
Data curation research was active in 1970s and 80s, as storage challenges began to emerge, with a focus on the design and use of relational databases. Research also investigated security and protection of storage mediums. In the 1990s, the focus on relational databases continued, aimed at incorporating greater domain semantics and making querying easier for users. New data storage technologies, such as data warehouses, continue to be studied. The recent focus on data science and data analytics has led to much work on machine learning, requiring large amounts of training and execution data.
2.4 Consume
Consumption is an activity that results from the application of data management principles and techniques, in which the data is analyzed and processed to answer questions, generate inferences, and draw insights. This phase involves tasks for preparing curated data so it becomes ready for consumption. The consumption includes preparation of curated data for analytics tasks, including assessing the quality of data before use, processing, and transformation. It may be supported by applications and techniques, including natural language processing (NLP), data mining, or machine learning. Important aspects of consumption are data re-representation and visualization.
With the introduction of online systems in the 2000s, research moved from supporting single decision-making tasks with structured data towards the development of applications for processing structured and unstructured data, independent of decision tasks. This data originates from traditional relational databases as well as from social media, log files, and technical reports. Preparation of structured, semi-structured and unstructured data for consumption by statistical methods including data mining became a focused topic in IS research. Recently, theory-driven research has started to pose constraints on preparation of data for consumption. Generally, data consumption has become more sophisticated in its data representation, visualization, transformation, and processing. Increasingly, mathematically formalized models with strong technical realizations are being investigated to allow for deeper insights into the datasets and better control of data usage in subsequent data analysis.
2.5 Control
Control is the activity that establishes security policies, institutes governance protocols, and aligns other activities of data management (the other Cs). It includes the legal, ethical, strategic, and other objectives and values of an organization. Techniques and approaches to control involve: establishing security rules and mechanisms of enforcement, institutional structures around data management, and monitoring and policing them to conform to organizational and higher-level mandates. Recognition of the need for effective control of data has led to the development of both technical and managerial techniques, including cryptography, blockchain, numerical analysis, separation of duties, and data audits.
The topic of control saw widespread focus in the 1980s, declined in the 1990s and became essentially non-existent in the 2000s. Early MIS Quarterly papers related to control explored the role of the data manager. Research in the 1980s to 1990s moved the discussion to the structure level, identifying which parts of the data management function should be centralized or decentralized. The conversation on these topics now has a wider scope, since research is no longer concerned with centralization or decentralization of data processing, but rather, with centralization or decentralization of overall information management functions. Today, the role of the data manager and how audits should be conducted have generally been formalized in standards, thus highlighting the importance of the data management function. Research on control now takes a more holistic approach, recognizing that one does not control data management as much as one controls and manages the organizational resources. In this way, it becomes more aligned with the consumption of data and other organizational resources.
4. CONCLUSION
Data management has progressed from traditional transaction processing to become a major organizational asset and basis for decision-making in society. With continued automated capture, increasing processing capabilities, and transmission of large amounts of data in multiple data formats, this topic will, undoubtedly, continue increasing in importance. This curation reflects the vast work on data management that has been carried out as the field of information systems has progressed. The research is organized around the themes identified as the 5Cs of Data Management. Of the five themes, conceptualize has been researched the most consistently over time, whereas the other four have evolved in different ways. More generally, the themes reflected the evolution of information technologies and changing interests and priorities of organizations.
Please cite this curation as follows: Chua, C., Indulska, M., Lukyanenko, R., Maass, W., Storey, V.C., “Data Management,” in MIS Quarterly Research Curations, Andrew Burton-Jones and Priya Seetharaman, Eds., http://misq.org/research-curations, February 14, 2022.
APPENDIX: MIS Quarterly Research Papers on Data Management
|
Paper |
Conceptualize |
Collect |
Curate |
Consume |
Control |
Method(s) Used |
|
Fang et al. (2021) |
|
|
|
x |
|
Design science, machine learning, machine learning experiments |
|
Recker et al. (2021) |
x |
|
x |
|
|
Literature review and analysis, conceptual framework |
|
Shin et al. (2020) |
|
x |
x |
x |
|
Design science, machine learning, machine learning experiments, econometric modeling |
|
Son et al. (2020) |
|
x |
x |
x |
|
Design science, machine learning, machine learning experiments, econometric modeling |
|
Malgonde et al. (2020) |
|
|
|
x |
|
Design science, agent-based simulation modeling |
|
Arazy et al. (2020) |
|
x |
x |
x |
|
Econometric modeling |
|
Lukyanenko et al. (2019) |
x |
x |
|
|
|
Laboratory experiment, field experiment, applicability check, expert study, machine learning experiment, design science |
|
Bera et al. (2019) |
x |
|
|
|
|
Eye tracking, laboratory experiments |
|
Qu and Jiang (2019) |
|
|
x |
|
|
Mathematical modeling |
|
Samuel et al. (2018) |
x |
|
|
|
|
Laboratory experiment, applicability check |
|
Abbasi et al. (2014) |
|
|
x |
x |
|
Design science, machine learning, machine learning experiments, field experiments |
|
Burton-Jones et al. (2017) |
x |
|
|
|
|
Literature review and analysis |
|
Ghose and Todri-Adamopoulos (2016) |
|
|
|
x |
|
Econometric modeling, quasi-experiment |
|
Saboo et al. (2016) |
|
|
|
x |
|
Econometric modeling |
|
Brynjolfsson et al. (2016) |
|
x |
x |
|
|
Laboratory experiments, replication studies |
|
Shi et al. (2016) |
|
x |
x |
x |
|
Design science, econometric modeling |
|
Chou et al. (2014) |
x |
|
|
|
|
Design science, delphi method, survey |
|
Kallinikos et al. (2013) |
x |
|
|
x |
|
Conceptual |
|
Chen et al. (2013) |
x |
|
|
|
|
Design science, action research |
|
Shanks and Weber (2012) |
x |
|
|
|
|
Conceptual |
|
Chau and Xu (2012) |
x |
x |
x |
x |
|
Design science, visualized clusters |
|
Chen et al. (2012) |
x |
|
|
|
|
Conceptual |
|
VanderMeer et al. (2012) |
|
x |
x |
|
|
Design science, experiment, field experiment |
|
Shmueli and Koppius (2011) |
|
|
x |
x |
|
Conceptual |
|
Recker et al. (2011) |
x |
|
|
|
|
Survey |
|
Bera et al. (2011) |
x |
|
|
|
|
Design science, experiment |
|
Shanks et al. (2008) |
x |
|
|
|
|
Experiment |
|
Abbasi and Chen (2008) |
x |
x |
x |
x |
|
Machine learning, experiment |
|
Parsons and Wand (2008) |
x |
|
|
|
|
Design science, panel |
|
Kuechler and Vaishnavi (2006) |
x |
|
|
|
|
Experiment |
|
Shaft and Vessey (2006) |
x |
|
|
|
|
Experiment |
|
Allen et al. (2006) |
|
x |
x |
x |
|
Conceptual |
|
Allen and March (2006) |
x |
|
x |
|
|
Conceptual, experiment |
|
Albert et al. (2004) |
x |
x |
x |
x |
|
Design science, case study |
|
Lindgren et al. (2004) |
|
x |
x |
|
|
Action research |
|
Speier and Morris (2003) |
|
|
x |
x |
|
Research model (hypothesis development), , experiment |
|
Tillquist et al. (2002) |
x |
|
|
|
|
Design science, exemplification |
|
Wixom and Watson (2001) |
|
|
x |
|
|
Research model, survey |
|
Cooper et al. (2000) |
|
|
x |
x |
|
Case study |
|
Mennecke et al. (2000) |
|
|
|
x |
|
Research model, experiment |
|
Jain et al. (1998) |
|
x |
|
|
x |
Conceptual model, survey |
|
Klein et al. (1997) |
|
|
|
x |
x |
Propositions, lab experiment |
|
Vandenbosch and Huff (1997) |
|
|
|
x |
|
Research model, field study |
|
Watson and Frolick (1993) |
x |
|
|
|
|
Interview, survey |
|
Storey and Goldstein (1993) |
x |
|
x |
|
|
Literature review and analysis |
|
Chan et al. (1993) |
x |
|
x |
|
|
Research model, experiment |
|
Goodhue et al. (1992a) |
x |
|
|
|
x |
Case study, propositions |
|
Byrd et al. (1992) |
x |
|
|
|
|
Literature review and analysis |
|
Goodhue et al. (1992b) |
|
|
|
x |
|
Conceptual |
|
Bieber and Kimbrough (1992) |
x |
|
|
|
|
Conceptual, exemplification |
|
Wetherbe (1991) |
x |
|
|
|
|
Key Failure Analysis |
|
Hansen and Hill (1989) |
|
x |
|
|
x |
Design Science |
|
Taylor and Tucker (1989) |
|
|
|
|
x |
Key Success Factor Analysis |
|
Liang (1988) |
x |
|
|
|
|
Design Science, Conceptual Framework |
|
Goodhue et al. (1988) |
x |
x |
x |
|
|
Case studies, Data Management Framework, Data Planning |
|
Hackathorn and Karimi (1988) |
x |
|
|
|
|
Comparative Method Analysis |
|
Ahituv and Zelek (1987) |
|
x |
|
|
x |
Statistical System Analysis |
|
Necco et al. (1987) |
x |
|
|
|
|
Survey, Key Factor Analysis |
|
Mantha (1987) |
x |
|
|
|
|
Quasi-Experiment, Data Modelling |
|
Gorr (1986) |
x |
x |
|
|
|
Knowledge Representation Method, Case Study |
|
Specht (1986) |
x |
|
|
x |
|
Field Study |
|
Montazemi and Conrath (1986) |
x |
x |
|
x |
|
Cognitive Mapping |
|
Ballou and Tayi (1985) |
x |
x |
x |
x |
x |
Conceptual Framework, Case Study |
|
Gillenson (1985) |
|
|
|
|
x |
Survey |
|
Colter (1984) |
x |
|
|
|
|
Conceptual Framework, System Analysis |
|
De and Sen (1984) |
x |
|
x |
|
|
Requirements Analysis, Case Study |
|
Batiste and Jung (1984) |
x |
|
|
|
|
Requirements Analysis |
|
Vanecek et al. (1983) |
|
|
|
|
x |
Design Science |
|
Vassiliou et al. (1983) |
|
|
x |
x |
|
Laboratory Studies |
|
Martin (1983) |
x |
|
|
x |
|
Critical Success Factors study and survey |
|
Watson and Driver (1983) |
|
|
|
x |
|
Experiment |
|
Culnan (1983) |
|
|
|
|
x |
Field study |
|
Edelman (1981) |
|
|
x |
x |
|
Framework development |
|
Merten and Severance (1981) |
|
x |
|
|
x |
Survey |
|
Semprevivo (1980) |
x |
x |
|
|
|
Case study |
|
Murray (1979) |
|
|
x |
|
x |
Tutorial as related to data security ? |
|
Wetherbe and Whitehead (1977) |
|
|
|
|
x |
Contingency theory management applied to ERP function |
|
Getz (1977) |
|
|
|
x |
|
Coalescence of data asset |
|
Juergens (1977) |
x |
|
|
|
|
General model of information systems development process |
|
Kling (1977) |
|
|
|
x |
|
Develops framework for software design groups |
Curated References
Abbasi, A., and Chen, H. 2008. “CyberGate: A Design Framework and System for Text Analysis of Computer-Mediated Communication,” MIS Quarterly (32:4), pp. 811–837. Also available at https://aisel.aisnet.org/misq/vol32/iss4/10/.
Abbasi, A., Zhou, Y., Deng, S., and Zhang, P. 2014. “Text Analytics to Support Sense-Making in Social Media: A Language-Action Perspective,” MIS Quarterly (42:2), pp. 427–464. Also available at https://aisel.aisnet.org/misq/vol42/iss2/6/.
Ahituv, N., and Zelek, M. 1987. “Instant Quality Control of Large Batch Processing Jobs,” MIS Quarterly (11:3), pp. 313–323. Also available at https://aisel.aisnet.org/misq/vol11/iss3/4/.
Albert, T. C., Goes, P. B., and Gupta, A. 2004. “GIST: A Model for Design and Management of Content and Interactivity of Customer-Centric Web Sites,” MIS Quarterly (28:2), pp. 161–182. Also available at https://aisel.aisnet.org/misq/vol28/iss2/3/.
Allen, G. N., Burk, D. L., and Davis, G. B. 2006. “Academic Data Collection in Electronic Environments: Defining Acceptable Use of Internet Resources,” MIS Quarterly (30:3), pp. 599–610. Also available at https://aisel.aisnet.org/misq/vol30/iss3/4/.
Allen, G. N., and March, S. T. 2006. “The Effects of State-Based and Event-Based Data Representation on User Performance in Query Formulation Tasks,” MIS Quarterly (30:2), pp. 269–290. Also available at https://aisel.aisnet.org/misq/vol30/iss2/5/.
Arazy, O., Lindberg, A., Rezaei, M., and Samorani, M. 2020. “The Evolutionary Trajectories of Peer-Produced Artifacts: Group Composition, the Trajectories’ Exploration, and the Quality of Artifacts,” MIS Quarterly (44:4), pp. 2013–2053. Also available at https://aisel.aisnet.org/misq/vol44/iss4/18/.
Ballou, D. P., and Tayi, G. K. 1985. “Reconciliation Process for Data Management in Distributed Environments,” MIS Quarterly (9:2), pp. 97–108. Also available at https://aisel.aisnet.org/misq/vol9/iss2/1/
Batiste, J. L., and Jung, J. T. 1984. “Requirements, Needs, and Priorities: A Structured Approach for Determining MIS Project Definition,” MIS Quarterly (8:4), pp. 215–227. Also available at https://aisel.aisnet.org/misq/vol8/iss4/1/.
Bera, P., Burton-Jones, A., and Wand, Y. 2011. “Guidelines for Designing Visual Ontologies to Support Knowledge Identification,” MIS Quarterly (35:4), pp. 883–908. Also available at https://aisel.aisnet.org/misq/vol35/iss4/6/.
Bera, P., Soffer, P., and Parsons, J. 2019. “Using Eye Tracking to Expose Cognitive Processes in Understanding Conceptual Models,” MIS Quarterly (43:4), pp. 1105–1126. Also available at https://aisel.aisnet.org/misq/vol43/iss4/6/.
Bieber, M. P., and Kimbrough, S. O. 1992. “On Generalizing the Concept of Hypertext,” MIS Quarterly (16:1), pp. 77–93. Also available at https://aisel.aisnet.org/misq/vol16/iss1/4/.
Brynjolfsson, E., Geva, T., and Reichman, S. 2016. “Crowd-Squared: Amplifying the Predictive Power of Search Trend Data,” MIS Quarterly (40:4), pp. 941–961. Also available at https://aisel.aisnet.org/misq/vol40/iss4/9/.
Burton-Jones, A., Recker, J., Indulska, M., Green, P., and Weber, R. 2017. “Assessing Representation Theory with a Framework for Pursuing Success and Failure,” MIS Quarterly (41:4), pp. 1307–1333. Also available at https://aisel.aisnet.org/misq/vol41/iss4/15/.
Byrd, T. A., Cossick, K. L., and Zmud, R. W. 1992. “A Synthesis of Research on Requirements Analysis and Knowledge Acquisition Techniques,” MIS Quarterly (16:1), pp. 117–138. Also available at https://aisel.aisnet.org/misq/vol16/iss1/6/.
Chan, H. C., Wei, K. K., and Siau, K. L. 1993. “User-Database Interface: The Effect of Abstraction Levels on Query Performance,” MIS Quarterly (17:4), pp. 441–464. Also available at https://aisel.aisnet.org/misq/vol17/iss4/4/.
Chau, M., and Xu, J. 2012. “Business Intelligence in Blogs: Understanding Consumer Interactions and Communities,” MIS Quarterly (36:4), pp. 1189–1216. Also available at https://aisel.aisnet.org/misq/vol36/iss4/17/.
Chen, H., Chiang, R. H. L., and Storey, V. C. 2012. “Business Intelligence and Analytics: From Big Data to Big Impact,” MIS Quarterly (36:4), pp. 1165–1188. Also available at https://aisel.aisnet.org/misq/vol36/iss4/16/
Chen, R., Sharman, R., Rao, H. R., and Upadhyaya, S. J. 2013. “Data Model Development for Fire Related Extreme Events: An Activity Theory Approach,” MIS Quarterly (37:1), pp. 125–147. Also available at https://aisel.aisnet.org/misq/vol37/iss1/7/.
Chou, C.-H., Zahedi, F. M., and Zhao, H. 2014. “Ontology-Based Evaluation of Natural Disaster Management Websites: A Multistakeholder Perspective,” MIS Quarterly (38:4), pp. 997–1016. Also available at https://aisel.aisnet.org/misq/vol38/iss4/5/.
Chua, C. E. H., Lim, W. K., Soh, C., and Sia, S. K. 2012. “Enacting Clan Control In Complex IT Projects,” MIS Quarterly (36:2), pp. 577–600. Also available at https://aisel.aisnet.org/misq/vol36/iss2/13/.
Colter, M. A. 1984. “A Comparative Examination of Systems Analysis Techniques,” MIS Quarterly (8:1), pp. 51–66. Also available at https://aisel.aisnet.org/misq/vol8/iss1/5/.
Cooper, B. L., Watson, H. J., Wixom, B. H., and Goodhue, D. 2000. “Data Warehousing Supports Corporate Strategy at First American Corporation,” MIS Quarterly (24:4), pp. 547–567. Also available at https://aisel.aisnet.org/misq/vol24/iss4/6/.
Culnan, M. J. 1983. “Chauffeured Versus End User Access to Commercial Databases,” MIS Quarterly (7:1), pp. 55–67. Also available at https://aisel.aisnet.org/misq/vol7/iss1/5/.
De, P., and Sen, A. 1984. “A New Methodology for Database Requirements Analysis,” MIS Quarterly (8:3), pp. 179–193. Also available at https://aisel.aisnet.org/misq/vol8/iss3/4/.
Edelman, F. 1981. “The Management of Information Resources - A Challenge for American Business,” MIS Quarterly (5:1), pp. 17–27. Also available at https://aisel.aisnet.org/misq/vol5/iss1/2/.
Fang, X., Gao, Y., and Jen-Hwa Hu, P. 2021. “A Prescriptive Analytics Method for Cost Reduction in Clinical Decision Making,” MIS Quarterly (45:1), pp. 83–115. Also available at https://aisel.aisnet.org/misq/vol45/iss1/5/.
Getz, C. W. 1977. “COALESCENCE: The Inevitable Fate of Data Processing,” MIS Quarterly (1:2), pp. 21–30. Also available at https://aisel.aisnet.org/misq/vol1/iss1/5/.
Ghose, A., and Todri-Adamopoulos, V. 2016. "Toward a Digital Attribution Model: Measuring the Impact of Display Advertising on Online Consumer Behavior," MIS Quarterly (40:4), pp. 889-910. Also available at https://aisel.aisnet.org/misq/vol40/iss4/7/
Gillenson, M. 1985. “Trends in Data Administration: 1981-1985,” MIS Quarterly (9:4), pp. 317–325. Also available at https://aisel.aisnet.org/misq/vol9/iss4/4/.
Goodhue, D. L., Kirsch, L. J., Quillard, J. A., and Wybo, M. D. 1992. “Strategic Data Planning: Lessons From the Field,” MIS Quarterly (16:1), pp. 11–34. Also available at https://aisel.aisnet.org/misq/vol16/iss1/1/.
Goodhue, D. L., Quillard, J. A., and Rockart, J. F. 1988. “Managing the Data Resource: A Contingency Perspective,” MIS Quarterly (12:3), pp. 373–392. Also available at https://aisel.aisnet.org/misq/vol12/iss3/2/.
Gorr, W. L. 1986. “Special Event Data in Shared Databases,” MIS Quarterly (10:3), pp. 239–255. Also available at https://aisel.aisnet.org/misq/vol10/iss3/4
Hackathorn, R. D., & Karimi, J. (1988). A framework for comparing information engineering methods. MIS Quarterly (12:2), pp. 203–220. Also available at https://aisel.aisnet.org/misq/vol12/iss2/4/.
Hansen, J. V, and Hill, N. C. 1989. “Control and Audit of Electronic Data Interchange,” MIS Quarterly (13:4), pp. 403–413. Also available at https://aisel.aisnet.org/misq/vol13/iss4/2/.
Jain, H., Ramamurthy, K., Ryu, H.-S., and Yasai-Ardekani, M. 1998. “Success of Data Resource Management in Distributed Environments: An Empirical Investigation,” MIS Quarterly (22:1), pp. 1–29. Also available at https://aisel.aisnet.org/misq/vol22/iss1/4/.
Juergens, H. F. 1977. “Attributes of Information System Development,” MIS Quarterly (1:2), pp. 31–44. Also available at https://aisel.aisnet.org/misq/vol1/iss1/6/.
Kallinikos, J., Aaltonen, A., and Marton, A. 2013. “The Ambivalent Ontology of Digital Artifacts,” MIS Quarterly (37:2), pp. 357–370. Also available at https://aisel.aisnet.org/misq/vol37/iss2/4/.
Klein, B. D., Goodhue, D. L., and Davis, G. B. 1997. “Can Humans Detect Errors in Data? Impact of Base Rates, Incentives, and Goals,” MIS Quarterly (21:2), pp. 169–194. Also available at https://aisel.aisnet.org/misq/vol21/iss2/2/.
Kling, R. 1977. “The Organizational Context of User-Centered Software Designs,” MIS Quarterly (1:4), pp. 41–52. Also available at https://aisel.aisnet.org/misq/vol1/iss1/14/.
Kuechler, W. L., and Vaishnavi, V. 2006. “So, Talk to Me: The Effect of Explicit Goals on the Comprehension of Business Process Narratives,” MIS Quarterly (30:4), pp. 961–979. Also available at https://aisel.aisnet.org/misq/vol30/iss4/10/.
Liang, T.-P. 1988. “Model Management for Group Decision Support,” MIS Quarterly (12:4), pp. 667–680. Also available at https://aisel.aisnet.org/misq/vol12/iss4/9/.
Lindgren, R., Henfridsson, O., and Schultze, U. 2004. “Design Principles for Competence Management Systems: A Synthesis of an Action Research Study,” MIS Quarterly (28:3), pp. 435–472. Also available at https://aisel.aisnet.org/misq/vol28/iss3/6/.
Lukyanenko, R., Parsons, J., Wiersma, Y. F., and Maddah, M. 2019. “Expecting the Unexpected: Effects of Data Collection Design Choices on the Quality of Crowdsourced User-Generated Content,” MIS Quarterly (43:2), pp. 623–648. Also available at https://aisel.aisnet.org/misq/vol43/iss2/14/.
Malgonde, O., Zhang, H., Padmanabhan, B., and Limayem, M. 2020. “Taming the Complexity in Search Matching: Two-Sided Recommender Systems on Digital Platforms,” MIS Quarterly (44:1), pp. 49–84. Also available at https://aisel.aisnet.org/misq/vol44/iss1/5/.
Mantha, R. W. 1987. “Data Flow and Data Structure Modeling for Database Requirements Determination: A Comparative Study,” MIS Quarterly (11:4), pp. 531–545. Also available at https://aisel.aisnet.org/misq/vol11/iss4/7/.
Martin, E. W. 1983. “Information Needs of Top MIS Managers,” MIS Quarterly (7:3), pp. 1–11. Also available at https://aisel.aisnet.org/misq/vol7/iss3/1/.
Mennecke, B. E., Crossland, M. D., and Killingsworth, B. L. 2000. “Is a Map More than a Picture? The Role of SDSS Technology, Subject Characteristics, and Problem Complexity on Map Reading and Problem Solving,” MIS Quarterly (24:4), pp. 601–629. Also available at https://aisel.aisnet.org/misq/vol24/iss4/3/.
Merten, A. G., and Severance, D. G. 1981. “Data Processing Control: A State-of-the Art Survey of Attitudes and Concerns of DP Executives,” MIS Quarterly (5:2), pp. 11–32. Also available at https://aisel.aisnet.org/misq/vol5/iss2/2/.
Montazemi, A. R., and Conrath, D. W. 1986. “The Use of Cognitive Mapping for Information Requirements Analysis,” MIS Quarterly (10:1), pp. 45–56. Also available at https://aisel.aisnet.org/misq/vol10/iss1/3/.
Murray, T. 1979. “Cryptographic Protection of Computer-Based Data Files,” MIS Quarterly (3:1), pp. 21–28. Also available at https://aisel.aisnet.org/misq/vol3/iss1/3/.
Necco, C. R., Gordon, C. L., and Tsai, N. W. 1987. “Systems Analysis and Design: Current Practices,” MIS Quarterly (11:4), pp. 461–476. Also available at https://aisel.aisnet.org/misq/vol11/iss4/3/.
Parsons, J., and Wand, Y. 2008. “Using Cognitive Principles to Guide Classification in Information Systems Modeling,” MIS Quarterly (32:4), pp. 839–868. Also available at https://aisel.aisnet.org/misq/vol32/iss4/11/.
Qu, X. (Shawn), and Jiang, Z. 2019. “A Time-Based Dynamic Synchronization Policy for Consolidated Database Systems,” MIS Quarterly (43:4), pp. 1041–1057. Also available at https://aisel.aisnet.org/misq/vol43/iss4/3/.
Recker, J., Lukyanenko, R., Jabbari, M., Samuel, B. M., and Castellanos, A. 2021. “From Representation to Mediation: A New Agenda for Conceptual Modeling Research in a Digital World,” MIS Quarterly (45:1), pp. 269–300. Also available at https://aisel.aisnet.org/misq/vol45/iss1/10/.
Recker, J., Rosemann, M., Green, P., and Indulska, M. 2011. “Do Ontological Deficiencies in Modeling Grammars Matter?,” MIS Quarterly (35:1), pp. 57–79. Also available at https://aisel.aisnet.org/misq/vol35/iss1/6/.
Saboo, A. R., Kumar, V., and Park, I. 2016. “Using Big Data to Model Time-Varying Effects for Marketing Resource (Re)Allocation,” MIS Quarterly (40:4), pp. 911–940. Also available at https://aisel.aisnet.org/misq/vol40/iss4/8/.
Samuel, B. M., Khatri, V., and Ramesh, V. 2018. “Exploring the Effects of Extensional Versus Intensional Representations on Domain Understanding,” MIS Quarterly (42:4), pp. 1187–1209. Also available at https://aisel.aisnet.org/misq/vol42/iss4/10/.
Semprevivo, P. 1980. “Incorporating Data Dictionary/Directory and Team Approaches into the Systems Development Process,” MIS Quarterly (4:3), pp. 1–15.
Shaft, T. M., and Vessey, I. 2006. “The Role of Cognitive Fit in the Relationship between Software Comprehension and Modification,” MIS Quarterly (30:1), pp. 29–55. Also available at https://aisel.aisnet.org/misq/vol30/iss1/4/.
Shanks, G., Tansley, E., Nuredini, J., Tobin, D., and Weber, R. 2008. “Representing Part-Whole Relations in Conceptual Modeling: An Empirical Evaluation,” MIS Quarterly (32:3), pp. 553–573. Also available at https://aisel.aisnet.org/misq/vol32/iss3/7/.
Shanks, G., and Weber, R. 2012. “The Hole in the Whole: A Response to Allen and March,” MIS Quarterly (36:3), pp. 965–980. Also available at https://aisel.aisnet.org/misq/vol36/iss3/17/.
Shi, Z. (Michael), Lee, G. M., and Whinston, A. B. 2016. “Toward a Better Measure of Business Proximity: Topic Modeling for Industry Intelligence,” MIS Quarterly (40:4), pp. 1035–1056. Also available at https://aisel.aisnet.org/misq/vol40/iss4/13/.
Shin, D., He, S., Lee, G. M., Whinston, A. B., Cetintas, S., and Lee, K.-C. 2020. “Enhancing Social Media Analysis with Visual Data Analytics: A Deep Learning Approach,” MIS Quarterly (44:4), pp. 1459–1492. Also available at https://aisel.aisnet.org/misq/vol44/iss4/3/.
Shmueli, G., and Koppius, O. R. 2011. “Predictive Analytics in Information Systems Research,” MIS Quarterly (35:3), pp. 553–572. Also available at https://aisel.aisnet.org/misq/vol35/iss3/5/.
Son, J., Flatley Brennan, P., and Zhou, S. 2020. “A Data Analytics Framework for Smart Asthma Management Based on Remote Health Information Systems with Bluetooth-Enabled Personal Inhalers,” MIS Quarterly (44:1), pp. 285–303. Also available at https://aisel.aisnet.org/misq/vol44/iss1/13/.
Specht, P. H. 1986. “Job Characteristics as Indicants of CBIS Data Requirements,” MIS Quarterly (10:3), pp. 271–287. Also available at https://aisel.aisnet.org/misq/vol10/iss3/6/.
Speier, C., and Morris, M. G. 2003. “The Influence of Query Interface Design on Decision-Making Performance,” MIS Quarterly (27:3), pp. 397–423. Also available at https://aisel.aisnet.org/misq/vol27/iss3/4/.
Storey, V. C., and Goldstein, R. C. 1993. “Knowledge-Based Approaches to Database Design,” MIS Quarterly (17:1), pp. 25–46. Also available at https://aisel.aisnet.org/misq/vol17/iss1/2/.
Taylor, J. R., and Tucker, C. C. 1989. “Reducing Data Processing Costs Through Centralized Procurement,” MIS Quarterly (13:4), pp. 487–499. Also available at https://aisel.aisnet.org/misq/vol13/iss4/8/.
Tillquist, J., King, J. L., and Woo, C. 2002. “A Representational Scheme for Analyzing Information Technology and Organizational Dependency,” MIS Quarterly (26:2), pp. 91–118. Also available at https://aisel.aisnet.org/misq/vol26/iss2/5/.
Vandenbosch, B., and Huff, S. L. 1997. “Searching and Scanning: How Executives Obtain Information from Executive Information Systems,” MIS Quarterly (21:1), pp. 81–107. Also available at https://aisel.aisnet.org/misq/vol21/iss1/4/.
VanderMeer, D., Dutta, K., and Datta, A. 2012. “A Cost-Based Database Request Distribution Technique for Online e-Commerce Applications,” MIS Quarterly (36:2), pp. 479–507. Also available at https://aisel.aisnet.org/misq/vol36/iss2/9/.
Vanecek, M. T., Solomon, I., and Mannino, M. V. 1983. “The Data Dictionary: An Evaluation from the EDP Audit Perspective,” MIS Quarterly (7:1), pp. 15–27. Also available at https://aisel.aisnet.org/misq/vol7/iss1/1/.
Vassiliou, Y., Jarke, M., Stohr, E. A., Turner, J. A., and White, N. H. 1983. “Natural Language for Database Queries: A Laboratory Study,” MIS Quarterly (7:4), pp. 47–61. Also available at https://aisel.aisnet.org/misq/vol7/iss4/5/.
Watson, C. J., and Driver, R. W. 1983. “The Influence of Computer Graphics on the Recall of Information,” MIS Quarterly (7:1), pp. 45–53. Also available at https://aisel.aisnet.org/misq/vol7/iss1/4/.
Watson, H. J., and Frolick, M. N. 1993. “Determining Information Requirements for an EIS,” MIS Quarterly (17:3), pp. 255–269. Also available at https://aisel.aisnet.org/misq/vol17/iss3/2/.
Wetherbe, J. C. 1991. “Executive Information Requirements: Getting It Right,” MIS Quarterly (15:1), pp. 51–65. Also available at https://aisel.aisnet.org/misq/vol15/iss1/4/.
Wetherbe, J. C., and Whitehead, C. J. 1977. “A Contingency View of Managing the Data Processing Organization,” MIS Quarterly (1:1), pp. 19–25. Also available at https://aisel.aisnet.org/misq/vol1/iss1/2/.
Wiener, M., Mähring, M., Remus, U., and Saunders, C. 2016. “Control Configuration and Control Enactment in Information Systems Projects: Review and Expanded Theoretical Framework,” MIS Quarterly (40:3), pp. 741-- D14. Also available at https://aisel.aisnet.org/misq/vol40/iss3/13/.
Wixom, B. H., and Watson, H. J. 2001. “An Empirical Investigation of the Factors Affecting Data Warehousing Success,” MIS Quarterly (25:1), pp. 17–41. Also available at https://aisel.aisnet.org/misq/vol25/iss1/2/.